Acquiring Digital Forensics Evidence
I detected malware on a user's system. It is clearly important to remove the malware from the user, run an up-to-date antimalware scan, and update the user's OS. But, it is also important to determine how this happened! So, I opened the file in a Windows VM and did some investigation
I had no luck opening up the file as it was hashed. So I created an image of the hard disk drive for further examination and To avoid an unintended change to the evidence.
I used a software called Autopsy to browse the disk image for evidence


With the forensics app, I was able to see the information, which is normally hidden from view.

I did a further investigation to find several records! Such as the Master Boot Record, and the boot volume that is hosting the OS files and applications with the user data!
I also explored the metadata. Criminal investigations can locate images of illegal activity or other information within metadata!
Within the Autopsy software, is a timeline! The timeline of file activity will help to reconstruct the pattern of events.
I was able to view a specific year and specify the month and even target the exact month>day>hour>minute>
Within this, I can see the exact time, location, and information of anything regarding the malware file I chose to scan

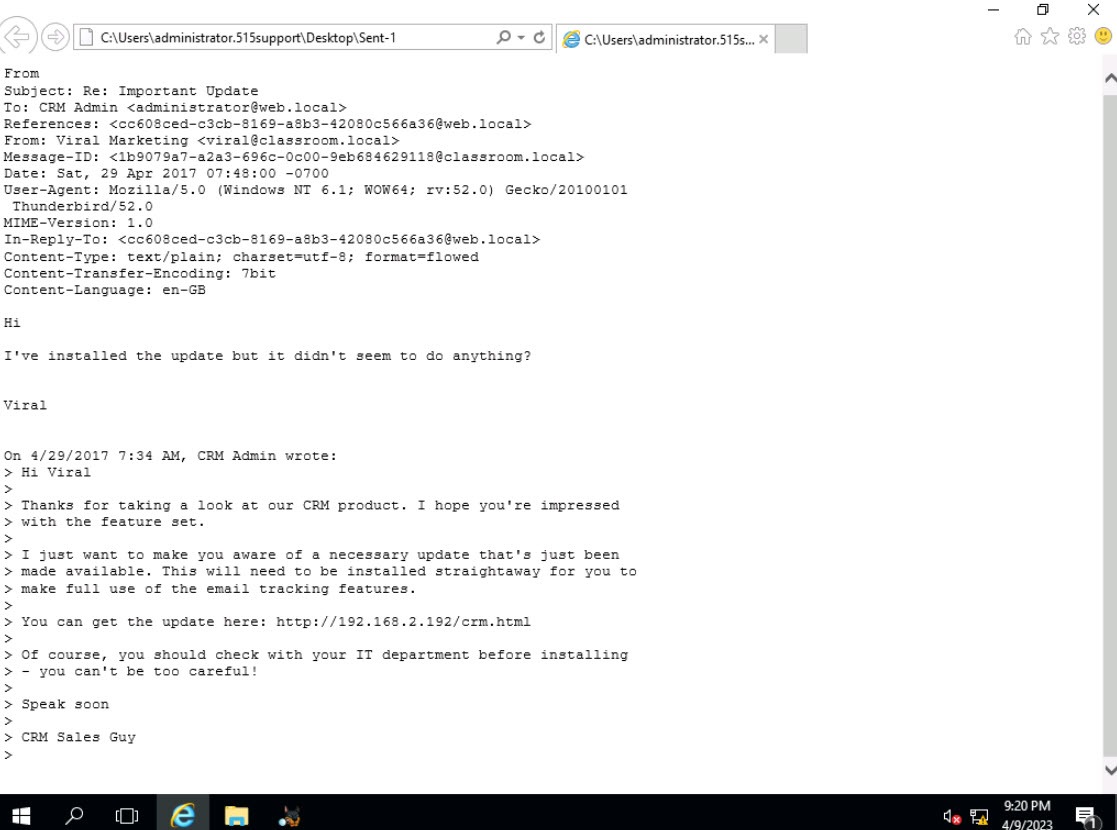
So, working as the security Admin I did just that. As pictured above, I was able to track down the exact date/time/and location that the phishing email was sent to someone on my network. I was able to read the content of the email from the sender with information regarding a request to install an update from a trusted source at http://192.168.2.192 and was tricked into downloading malware

At this time, Once I examined the email with the URL I extracted the file and saved it for further documentation, and can report this to a senior sec admin. I would then, of course, do further investigation.
In a situation like this one. the steps I would take is
-Isolate the machine the malware is on
-determine if any other users have been affected and make sure the malware is quarantined
-research the malware and see if any CVEs exist
-Block this URL from being accessed from our network by configuring my firewall on the network
-determine if any sensitive information has been compromised
-block this email sender if I determine that they are not a trusted source. This can be blocked for all users on the network as well if I configure it as the Admin.
-I would then sandbox the file, put it into a safe environment, and use the copy as I did in this exercise, and do further investigations.
-I also want to make sure that the user can be put back to work ASAP as well. So once I have the malicious file for my investigations, I would update, scan, and remove any malware on the user's device along with password changes and safe security practices implemented.
-And let's not forget, an educational opportunity for the user.
This is why running security audits on a business or agency is so important! Something such as phishing emails being sent out by the security admin regularly is so simple to determine if the network has any users that could be tricked. Furthering education for all the users on the network is the first step in stopping any attack.
Post a comment