Ettercap and ARP poisoning
We are using 2 machines for this exercise. I will be using windows to display the target host information and kali Linux for the offensive tasks
Firstly let's see what we have on our network. Using Windows Powershell admin on the attack target, we use the command arp -a. This shows the IP and MAC addresses of devices on your network, and the mac addresses that your IP has talked to recently

Here you can see, we found 4 hosts that our IP has connected with recently
This is a good tool to display if someone is on your network and who your IP has been talking to. Our target IP is 10.1.16.2 remember that :)
Let's fire up kali, and configure this attack

Here you can see information about the attacker. Note the IP address. 10.1.16.9 we are clearly on the network we need to be on!
Now let's launch a tool called ettercap,
It is preinstalled on many kali Linux VMs
we are using eth0 as the connection and we are sniffing the network to see what we find.
When would we use an eth connection? As security analysts, we could see what others have available on our own network. And as an offensive view, This could be used as an attacking connection if you are connecting directly to someone's network. Let's say a physical penetration test or finding an ethernet connection somewhere.
Because our kali box is on the network we simply open ettercap And start our scan
In the upper toolbar, we hit the hosts scan
And we now get 4 hosts!!! Let's view them.

Who are these hosts?
10.1.16.1 is a user
10.1.16.2 is a user
10.1.16.22 with a nmap I saw it to be a pfscense firewall
10.1.16.254 is the router and our connection to servers
In the Kali box, let's start targeting 10.1.16.2 the user, and 10.1.16.254 the router
Let's select them and add them to a target.
10.1.16.2 is target 1 and 10.1.16.254 is target 2

And we now start an ARP poison

Let's crack open wireshark and see what is happening.
Start capture on our eth0 connection and open a packet
Let's pick one labeled ARP.
address from our user 10.1.16.2 to our router 10.1.16.254 and see what it says


Hmm… duplicate IP address. So 2 hosts are using that same IP address. Thank you Ettercap on Wireshark hehe.
On the attacked computer, let's open PowerShell and check our arp info.
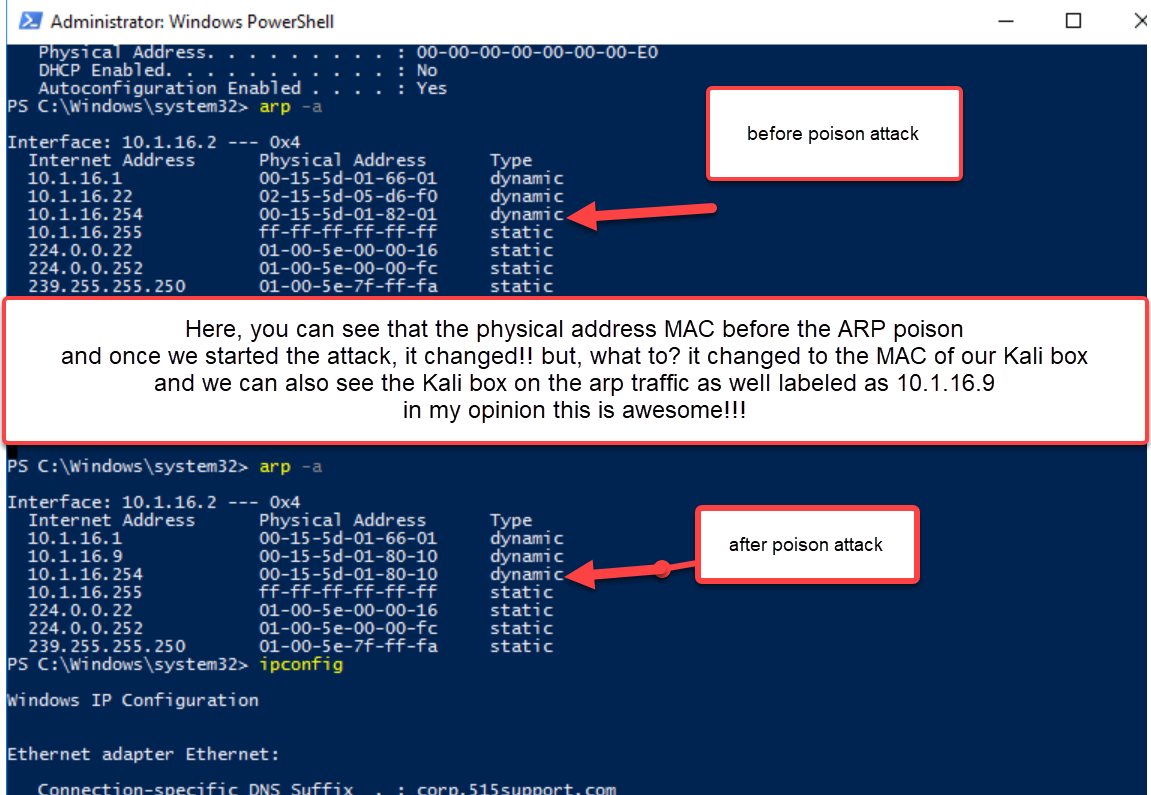
We stop the kali box ettercap and we delete the hosts off of the ettercap. It now “releases” those IP addresses.
So we run arp again and this is what we see.

The MAC addresses are back to normal!
If we have someone on our network. Conducting this attack they will be able to read and alter intercepted data allowing the user to have no idea that this is happening.
How can a defensive network or cybersecurity admin stop this? We can set an alert for these duplicated MAC addresses and conduct countermeasures With firewalls, we also have the capability to BLOCK certain IPs from even connecting in the future. The simple arp command is an amazing and simple command for windows platforms and is an awesome troubleshooting technique.

How did we determine it was associated to the kali box? With a nmap report, we see it is the kali box.
Post a comment